# CTF Recap #1
---
## Welcome

----
### Tools used:
* **file**
* classify file
* **exiftool**
* read metadata
* **binwalk**
* analyse binary data
* **unzip**
* extract compressed data
----
### Tools used:
* **base64**
* base64 decode data
* https://en.wikipedia.org/wiki/Base64
* **strings**
* printable characters of file
* **stegsolve**
* hidden text in img
* **gimp**
* image manipulation
---
## Magic PNGs

----
### PNG Structure

source: http://www.libpng.org
----
### PNG Chunks

source: http://www.libpng.org
----
### PNG Signature

source: http://www.libpng.org
----
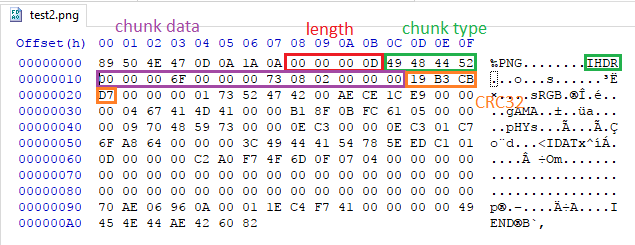
http://www.libpng.org/pub/png/spec/1.2/PNG-Structure.html
----
### Used Tools
* **google**
* PNG structure
* **xxd**
* binary -> hex
* **binwalk -W / colordiff**
* compare files
* **hexeditor**
* make changes to file
----
### PNG Tools
* **pngcheck**
* check validity of png
* **pnginfo**
* png information + errors
* **pngchunks**
* inspect single chunks
----
### PNG Information
* http://einstein.informatik.uni-oldenburg.de/rechnernetze/png.htm
* https://www.w3.org/TR/PNG-Chunks.html
* http://www.libpng.org/pub/png/spec/1.2/PNG-Structure.html
* http://www.libpng.org/pub/png/book/chapter08.html
---
<!-- .slide: data-background="https://media.giphy.com/media/hPrt0zRTMAVaugcgPf/giphy.gif" -->
<div style="color: #fff; font-size: 100px;">
Now it's your turn :)
</div>
----
Write-up link:
https://its.fh-campuswien.ac.at/hackmd/s/HJP-O1jUE#
{"title":"Example Slide","tags":"presentation","slideOptions":{"theme":"serif","previewLinks":true,"transition":"slide"}}